NST and Virtual Machines: Difference between revisions
(Added section on creating VMDK meta file) |
|||
| (5 intermediate revisions by one other user not shown) | |||
| Line 100: | Line 100: | ||
NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under. | NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under. | ||
== How do I update the VirtualBox Server Modules on Hypervisor (v5.0.x)? == | == How do I update the VirtualBox Server Modules on the Host Hypervisor (v5.0.x)? == | ||
Anytime you update the kernel on a Linux based system running VirtualBox v5.0.x, you will need to tell VirtualBox to rebuild its kernel modules. This can be done using the following command: | Anytime you update the kernel on a Linux based system running VirtualBox v5.0.x, you will need to tell VirtualBox to rebuild its kernel modules. This can be done using the following command: | ||
| Line 107: | Line 107: | ||
NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under. | NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under. | ||
== USB Access: VirtualBox 6.x or Greater == | |||
VMs running on VirtualBox 6.x or greater requires the user running the VirtualBox hypervisor to be added to the "'''vboxusers'''" group. In this example we will add the "'''nst'''" user to the "'''vboxusers'''" group. | |||
usermod -G vboxusers -a nst; | |||
= VMware Frequently Asked Questions = | = VMware Frequently Asked Questions = | ||
| Line 118: | Line 123: | ||
* You'd like to monitor the network traffic to and from a particular Windows machine, and you don't have the necessary hardware to tap into what's going across the Ethernet cable. By booting the Network Security Toolkit within a virtual machine on the Windows machine, you will be able to monitor the Ethernet traffic with tools such as wireshark, snort, ntop, etc. | * You'd like to monitor the network traffic to and from a particular Windows machine, and you don't have the necessary hardware to tap into what's going across the Ethernet cable. By booting the Network Security Toolkit within a virtual machine on the Windows machine, you will be able to monitor the Ethernet traffic with tools such as wireshark, snort, ntop, etc. | ||
* You are doing development on a Windows machine and would like to use some of the features from the Network Security Toolkit without using an additional machine (the Network Security Toolkit makes it pretty easy to setup a web server or SQL database in these situations). | * You are doing development on a Windows machine and would like to use some of the features from the Network Security Toolkit without using an additional machine (the Network Security Toolkit makes it pretty easy to setup a web server or SQL database in these situations). | ||
== How Do I Convert A Raw Disk Image To VMDK == | |||
It is fairly easy to make raw disk images using the dd command on a block device. While VirtualBox provides a fairly straight forward way to make use of raw disk images, VMware does not. You need to create a "meta" VMDK file to go with your disk image and upload both the raw disk image file into your virtual environment. For example, let's assume that you want to make a raw disk image of the USB drive that appears as /dev/sdb. You could run the following command: | |||
sudo dd status=progress if=/dev/sdb bs=$((1024 * 1024 * 4)) of=usb.img | |||
Now that you have your raw disk image (''usb.img''), you need to create a corresponding VMDK file describing the disk image. You can use the following bash script to accomplish this (copy the following to a file called ''create-vmdk.bash''). | |||
<syntaxhighlight lang="sh">#!/bin/bash | |||
declare fileName="${1}"; | |||
declare -i fileSize=${2:-$(stat --printf="%s" "$fileName" 2>/dev/null)}; | |||
if [ "${fileSize}" == "" ] || ((fileSize <= 0)); then | |||
echo -e " | |||
Usage: create-vmdk.bash FILE_NAME [FILE_SIZE] | |||
Where: FILE_NAME - Name of raw disk image file | |||
FILE_SIZE - Size of image in bytes | |||
" | |||
exit 1; | |||
fi | |||
# Helper method to generate VMDK descriptor for raw image | |||
# a raw disk image. See following URL with info about | |||
# VMDK files for raw disk images: | |||
# | |||
# https://communities.vmware.com/thread/533089 | |||
createVmdk() { | |||
declare file="${1}"; | |||
declare -i sizeBytes=${2}; | |||
declare -i sizeSectors=$((sizeBytes / 512)); | |||
declare -i sizeCylinders=$((sizeSectors / 16065)); | |||
declare cid="12345678"; | |||
declare bn="$(basename "${file}")"; | |||
echo -e "# Disk DescriptorFile | |||
version=1 | |||
encoding=\"UTF-8\" | |||
CID=${cid} | |||
parentCID=ffffffff | |||
createType=\"vmfs\" | |||
# Extent description | |||
RW ${sizeSectors} VMFS \"${bn}\" | |||
# The Disk Data Base | |||
#DDB | |||
ddb.virtualHWVersion = \"8\" | |||
ddb.geometry.cylinders = \"${sizeCylinders}\" | |||
ddb.geometry.heads = \"255\" | |||
ddb.geometry.sectors = \"63\" | |||
ddb.adapterType = \"lsilogic\""; | |||
} | |||
createVmdk "${fileName}" ${fileSize}; | |||
</syntaxhighlight> | |||
You can then invoke the script as follows to create ''usb.img.vmdk''. | |||
./create-vmdk.bash usb.img >| usb.img.vmdk | |||
Next, upload both the ''usb.img'' and ''usb.img.vmdk'' files to your VMware environment. If things work as they have in the past, you should have a new disk image available for use within your VMware environment that can be attached and detached to virtual machines as needed. | |||
== How Much Does It Cost? == | == How Much Does It Cost? == | ||
Latest revision as of 14:25, 22 January 2020
General Virtual Machine Questions
What Virtual Machines Will NST Run Under?
NST is currently known to run under:
- The VMware Product line.
- VirtualBox
What are the Disadvantages of Running NST within a Virtual Machine?
- Performance will be less than running NST on bare metal system (i.e., Running natively).
- Wireless tools will not work as physical wireless adapters appear are typically virtualized as Ethernet NICs.
What are the Advantages of Running NST within a Virtual Machine?
- You can monitor the traffic on the virtual machine network switches without any cables or hardware.
- You can easily move your NST system to a different machine.
Can I Run Virtual Machines from a NST System?
Yes. If you perform a full installation of NST, you can install a virtual environment and run virtual machines within your NST system. For example, if you install VirtualBox onto your NST system, it will be possible to run Operating Systems like "Windows 7" virtually within your NST system.
Both the VMware and VirtualBox environments are known to run on a NST system. Any virtual environment which runs under Fedora should work on a NST system as well.
VirtualBox Frequently Asked Questions
Why can't I monitor all traffic on the virtual network adapter?
There are two likely reasons that can trigger this issue:
1. The network adapter must be up and enabled on the host system before a virtualized NST system will be able to see any traffic on the adapter. If this is the issue, you will need to enable the network adapter on the machine which hosts the virtual NST (outside of the NST system).
2. VirtualBox allows one to specify the "virtual hardware implementation" when configuring network adapters. We have seen the case where some "virtual hardware implementations" do not properly support promiscuous mode operation within the NST environment (in particular some of the E1000 adapters).
So, if you run across this condition, we recommend that you try a different "virtual hardware implementation" (the PCnet Fast-III implementation has worked for us).
How do I install the VirtualBox Guest Additions?
- Install the following packages that are necessary to build the kernel modules:
yum install gcc kernel-devel
- From the Devices menu of VirtualBox, click on the Install Guest Additions options. If things go well, a virtual CD will appear on your GNOME desktop.
- Open a terminal window and login as root (if you aren't already logged in as root).
- Copy the contents of the CD to a temporary directory, run the installation script, and then remove the temporary directory (NOTE: While VBOX* will probably work as shown below, it is recommended to replace it with the actual directory name):
cp -rp /media/VBOX* /tmp/ cd /tmp/VBOX* ./VBoxLinuxAdditions-x86.run # NOTE: Run ./VBoxLinuxAdditions-amd64.run if 64 bit machine cd rm -fr /tmp/VBOX*
- Reboot the system (may not always be required - you can't do this step if running from a Live boot).
How do I update the VirtualBox Guest Additions?
Anytime you update the kernel on a NST system running under VirtualBox, you will need to rebuild the VirtualBox kernel module. This can be done using the following command:
service vboxadd setup
It's recommended to either reboot your machine or restart the VirtualBox services after rebuilding the kernel module. Here are the commands to restart the VirtualBox services:
service vboxadd restart service vboxadd-x11 restart service vboxadd-service restart
NOTE: You may or may not have the vboxadd-x11 service.
NOTE: Updating and restarting the services won't necessarily fix your current X session. So, if you are logged into a graphical desktop, you will need to log out and back in order to make use of the VirtualBox drivers.
How do I install VirtualBox Server onto a NST Distribution?
See the HowTo Install VirtualBox page for details.
How do I update the VirtualBox Server Modules on the Host Hypervisor (v3.1.x)?
Anytime you update the kernel on a Linux based system running VirtualBox v3.1.x, you will need to tell VirtualBox to rebuild its kernel modules. This can be done using the following command:
service vboxdrv setup;
NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under.
How do I update the VirtualBox Server Modules on the Host Hypervisor (v5.0.x)?
Anytime you update the kernel on a Linux based system running VirtualBox v5.0.x, you will need to tell VirtualBox to rebuild its kernel modules. This can be done using the following command:
/sbin/rcvboxdrv setup;
NOTE: This this is different than the "VirtualBox Guest Additions" as this refers to the native OS under which the VirtualBox environment is running under.
USB Access: VirtualBox 6.x or Greater
VMs running on VirtualBox 6.x or greater requires the user running the VirtualBox hypervisor to be added to the "vboxusers" group. In this example we will add the "nst" user to the "vboxusers" group.
usermod -G vboxusers -a nst;
VMware Frequently Asked Questions
Why Would I Want To Run NST Under VMware?
There are several reasons why one may want to boot the Network Security Toolkit from within a VMware virtual machine:
- You would like to have a full hard disk installation of the Network Security Toolkit, but don't want to re-partition your hard disk.
- You would simply like to try out a new Network Security Toolkit ISO distribution, but don't want to reboot your system. Using the free VMware Server or VMware Player, one can boot the Network Security Toolkit directly from the ISO file (you won't need to burn a disk).
- You'd like to monitor the network traffic to and from a particular Windows machine, and you don't have the necessary hardware to tap into what's going across the Ethernet cable. By booting the Network Security Toolkit within a virtual machine on the Windows machine, you will be able to monitor the Ethernet traffic with tools such as wireshark, snort, ntop, etc.
- You are doing development on a Windows machine and would like to use some of the features from the Network Security Toolkit without using an additional machine (the Network Security Toolkit makes it pretty easy to setup a web server or SQL database in these situations).
How Do I Convert A Raw Disk Image To VMDK
It is fairly easy to make raw disk images using the dd command on a block device. While VirtualBox provides a fairly straight forward way to make use of raw disk images, VMware does not. You need to create a "meta" VMDK file to go with your disk image and upload both the raw disk image file into your virtual environment. For example, let's assume that you want to make a raw disk image of the USB drive that appears as /dev/sdb. You could run the following command:
sudo dd status=progress if=/dev/sdb bs=$((1024 * 1024 * 4)) of=usb.img
Now that you have your raw disk image (usb.img), you need to create a corresponding VMDK file describing the disk image. You can use the following bash script to accomplish this (copy the following to a file called create-vmdk.bash).
#!/bin/bash
declare fileName="${1}";
declare -i fileSize=${2:-$(stat --printf="%s" "$fileName" 2>/dev/null)};
if [ "${fileSize}" == "" ] || ((fileSize <= 0)); then
echo -e "
Usage: create-vmdk.bash FILE_NAME [FILE_SIZE]
Where: FILE_NAME - Name of raw disk image file
FILE_SIZE - Size of image in bytes
"
exit 1;
fi
# Helper method to generate VMDK descriptor for raw image
# a raw disk image. See following URL with info about
# VMDK files for raw disk images:
#
# https://communities.vmware.com/thread/533089
createVmdk() {
declare file="${1}";
declare -i sizeBytes=${2};
declare -i sizeSectors=$((sizeBytes / 512));
declare -i sizeCylinders=$((sizeSectors / 16065));
declare cid="12345678";
declare bn="$(basename "${file}")";
echo -e "# Disk DescriptorFile
version=1
encoding=\"UTF-8\"
CID=${cid}
parentCID=ffffffff
createType=\"vmfs\"
# Extent description
RW ${sizeSectors} VMFS \"${bn}\"
# The Disk Data Base
#DDB
ddb.virtualHWVersion = \"8\"
ddb.geometry.cylinders = \"${sizeCylinders}\"
ddb.geometry.heads = \"255\"
ddb.geometry.sectors = \"63\"
ddb.adapterType = \"lsilogic\"";
}
createVmdk "${fileName}" ${fileSize};
You can then invoke the script as follows to create usb.img.vmdk.
./create-vmdk.bash usb.img >| usb.img.vmdk
Next, upload both the usb.img and usb.img.vmdk files to your VMware environment. If things work as they have in the past, you should have a new disk image available for use within your VMware environment that can be attached and detached to virtual machines as needed.
How Much Does It Cost?
While some of the VMware virtualization products do cost money, others like VMware Server and VMware Player do not. The choice is yours as NST should run within all of VMware's virtual environments.
What Version(s) of the NST Work Within VMware Virtualization Environments?
The 1.4.1 and later releases of the Network Security Toolkit should work very well as a guest OS within a VMware virtual environment. These newer releases of the Network Security Toolkit will include the nstvmware script and the open-vm-tools package to maximize the performance of the Network Security Toolkit when running from within a Virtual machine.
Are the VMware Tools & Modules Included?
Yes, starting with the 1.4.1 release of the Network Security Toolkit we have included the various kernel modules and utility programs necessary for optimal performance within a VMware virtual environment.
Starting with the 2.11.0 release of the NST package, these tools are found in the open-vm-tools package.
Is There a Pre-Built VMware NST Virtual Machine Available?
Yes. You should be able to find a pre-built version of the NST Virtual Machine on the project's download page. These downloads will be large ZIP files with a naming convention of: "nst-vm-VERSION.ARCH.zip" where VERSION corresponds to the NST release and ARCH corresponds to the hardware archecture. For example: nst-vm-2.13.0.i686.zip.
The 2.13.0 release of the NST was the first time that both a 32 bit (i686) and 64 bit (x86_64) pre-built NST virtual machine was made available for direct download.
How Do I Use the NST ISO in a VMware Virtual Machine?
If you've already downloaded the NST ISO image(s), you don't need to download the large pre-built NST virtual machine ZIP file(s). You can build your own NST virtual machine fairly simply using an NST ISO image.
In order to boot the Network Security Toolkit ISO image from within a VMware virtual machine, we recommend that you follow these steps:
- Install VMware Server or VMware Player onto your host system.
- Next download and unzip the "nst-vm-live-VERSION.ARCH.zip" file onto your host system. When this file is unzipped it will create a "nst-VERSION-ARCH" directory containing the necessary files to boot the Network Security Toolkit ISO image.
- Next, if necessary, download a ISO image of the Network Security Toolkit from NST project's download page. You can also download the ISO image directly from a running Network Security Toolkit system using the "Get CD/DVD/Device Image" page in the NST WUI (select System then File System Management from the main menu bar to find the link to the page).
- Copy (or move) the ISO image into the "nst-VERSION-ARCH" directory created by the extraction of the "nst-vm-live-VERSION.ARCH.zip" file.
- Start the VMware virtual environment using one of the provided .vmx files. There are many different VMware virtual environments, here are a couple of examples:
- Under Windows: double clicking on the "nst-vm-windows-2.11.0.vmx" icon (you may not see the ".vmx" extension).
- Linux users can start the VMware Player on the command line using the following:
[root@striker ~]# vmplayer nst-VERSION-ARCH/nst-vm-linux-VERSION.vmx &
If you intend to use the Network Security Toolkit for a extended period of time, we recommend that you use the install mode of the nstvmware script to install the distribution to a virtual hard disk. By doing a hard disk install in this manner, your changes will be kept permanently between reboots.
[root@probe ~]# nstvmware -m install -a toolkit -v
... Takes awhile and a lot of output is produced as NST
is installed from the virtual ISO image to the virtual
hard disk image ...
[root@probe ~]# poweroff
... System shuts down and the VMware Player terminates ...
![]() Using the "install" function of the nstvmware script assumes that a virtual hard disk will be available as /dev/sda. The entire virtual hard disk will be initialized. Any data you may have had on the virtual disk will be lost! Do not use this command if you have any information on the virtual disk you want to keep.
Using the "install" function of the nstvmware script assumes that a virtual hard disk will be available as /dev/sda. The entire virtual hard disk will be initialized. Any data you may have had on the virtual disk will be lost! Do not use this command if you have any information on the virtual disk you want to keep.
This will give your toolkit permanent storage and cause it to boot up directly into a graphical desktop login. You may delete or disconnect the ISO image from the virtual machine after installing to the virtual disk. If you do not remove or disconnect the ISO image from the virtual machine, you may need to adjust the "virtual BIOS" settings. To adjust the "virtual BIOS" settings, you'll need to press the "F2" key at the appropriate time - watch the boot screen closely.
After a hard disk install, the password will be reset to the factory default value of nst2003 (for NST distributions prior to 1.4.2 the default value is nst@2003).
Are There Limitations To Running NST In A VMware Virtual Environment?
There are several limitations that need to be considered when running the Network Security Toolkit under a VMware virtual environment.
- You can not directly access the hard disk of the host system. For example, you will not be able to create/modify the partition table of the host system.
- You can not access files on the host system outside of the virtual machine, unless your VMware environment supports it and you've taken the time to setup the shared folders. You can always use network shared folders and/or scp commands to transfer files between the host system and the virtual machine.
- Wireless features of the Network Security Toolkit will not be usable within a virtual machine as they tend to require direct access to the wireless adapters. However, you might be able to get around this limitation if you have a USB WIFI adapter supported by NST. We have not tried experimenting with USB WIFI adapters under VMware, so it might be possible.
- Your privilege level is limited to the user level that started the Network Security Toolkit Virtual Machine. You can not do anything within the Network Security Toolkit Virtual Machine which the user account used on the host machine is not allowed to do. For example, if you are using a "Limited Account" on a Windows XP machine, you will not be able to monitor all of the Ethernet traffic within the Network Security Toolkit Virtual Machine. In this case, the host operating system should limit you to monitoring the traffic which is to/from your virtual system.
What Does the nstvmware Script Do?
The nstvmware script has several modes of operation and facilitates common tasks that you are likely to perform when booting the Network Security Toolkit within a VMware virtual environment. In particular:
- It allows you to quickly setup a Network Security Toolkit system running within a VMware virtual machine.
- It allows you to easily install the Network Security Toolkit distribution from the booted ISO image onto a virtual disk.
- It allows you to quickly adjust the X settings for different environments. For example, if you have a laptop running at 1600x1200 with a 15.1 inch screen, try running: "nstvmware -m xorg.conf --width 1600 --height 1200 --diagonal 15.1", and then restart your X server.
- It allows you to increase the effective font size for the X display. For example, if you have a laptop running at 1600x1200 with a 15.1 inch screen, try running: "nstvmware -m xorg.conf --width 1600 --height 1200 --diagonal 12", and then restart your X server. In this case we are faking the screen dimension size smaller which has the effect of increasing the font size for the X display.
For further information on the nstvmware script, see the nstvmware man page.
How Do I Add More Than One Network Ethernet Adapter? (VMware Player: Windows)
A NST Virtual Machine running under VMware Player host control can utilize multiple network interfaces by running a different network/security application on each one of them.
The following sections cover the details on how to configure additional physical network adapters to be used with a NST Virtual Machine under a Windows-based VMware Player host.
The Windows "vmx" VMware Player configuration file: "nst-vm-windows-VERSION.vmx" has 4 network Ethernet interfaces already defined. Network interface: "eth0" will start in a "connected" state while network interfaces: "eth1", "eth2" and "eth3" will be started in the disconnected state. Network interface: "eth3" also has its "present" state set to "false". This allows for audio and sound usage with NST. If audio is not required, one can enable the "present" state to "true" for this interface. The connection type (connectionType) for each defined network Ethernet interface is set to: "custom".
The following shows the predefined Ethernet interface settings within the Windows "vmx" VMware Player configuration file: "nst-vm-windows-VERSION.vmx":
ethernet0.present = "TRUE" ethernet0.virtualDev = "vmxnet" ethernet0.startConnected = "TRUE" ethernet0.connectionType = "custom" ethernet0.vnet = "vmnet0" ethernet1.present = "TRUE" ethernet1.virtualDev = "vmxnet" ethernet1.startConnected = "FALSE" ethernet1.connectionType = "custom" ethernet1.vnet = "vmnet2" ethernet2.present = "TRUE" ethernet2.virtualDev = "vmxnet" ethernet2.startConnected = "FALSE" ethernet2.connectionType = "custom" ethernet2.vnet = "vmnet3" ethernet3.present = "FALSE" ethernet3.virtualDev = "vmxnet" ethernet3.startConnected = "FALSE" ethernet3.connectionType = "custom" ethernet3.vnet = "vmnet4"
***Note: One can also use the new vmxnet3 virtual network driver. Example for "eth0":
ethernet0.present = "TRUE" ethernet0.virtualDev = "vmxnet3" ethernet0.startConnected = "TRUE" ethernet0.connectionType = "custom" ethernet0.vnet = "vmnet0"
According to VMware: The VMXNET 3 adapter is the next generation of a paravirtualized NIC designed for performance, and is not related to VMXNET or VMXNET 2. It offers all the features available in VMXNET 2, and adds several new features like multiqueue support (also known as Receive Side Scaling in Windows), IPv6 offloads, and MSI/MSI-X interrupt delivery.
Each defined network adapter will assume a globally unique "MAC" address when the NST Virtual Machine is first booted up. This allows for multiple NST Virtual Machine instances to exist on the same physical network subnet without duplicate "ARP" entries being discovered.
The following shows an example of the globally unique "MAC" addresses and the "UUID" generated after the first time the NST Virtual Machine is started. This is typically generated at the end of the Windows "vmx" VMware Player configuration file: "nst-vm-windows-VERSION.vmx".
ethernet0.addressType = "generated" ethernet1.addressType = "generated" ethernet2.addressType = "generated" uuid.location = "56 4d 65 10 d6 b3 92 2d-ac ab 98 13 5e 8d e6 bb" uuid.bios = "56 4d 65 10 d6 b3 92 2d-ac ab 98 13 5e 8d e6 bb" ethernet0.generatedAddress = "00:0c:29:8d:e6:bb" ethernet0.generatedAddressOffset = "0" ethernet1.generatedAddress = "00:0c:29:8d:e6:c5" ethernet1.generatedAddressOffset = "10" ethernet2.generatedAddress = "00:0c:29:8d:e6:cf" ethernet2.generatedAddressOffset = "20"
A mapping for each physical network adapter to a VMware Player virtual network adapter needs to occur. The Windows "vmx" VMware Player configuration file: "nst-vm-windows-VERSION.vmx" has already defined the following logical Ethernet to virtual network adapter mapping:
- "eth0" <=> "vmnet0"
- "eth1" <=> "vmnet2"
- "eth2" <=> "vmnet3"
- "eth3" <=> "vmnet4"
Use the vmnetcfg.exe Windows VMware Player "Virtual Network Editor" found in the top level directory where the VMware Player was installed to perform the physical to virtual network adapter mapping. Each mapping will be associated with a "Bridged" connection type.
Lets use a Windows VMware Player host system configured with 2 physical network ethernet adapters (a "3Com" and a "Xircom CardBus" adapter) to demonstrate a physical to virtual network adapter mapping example:
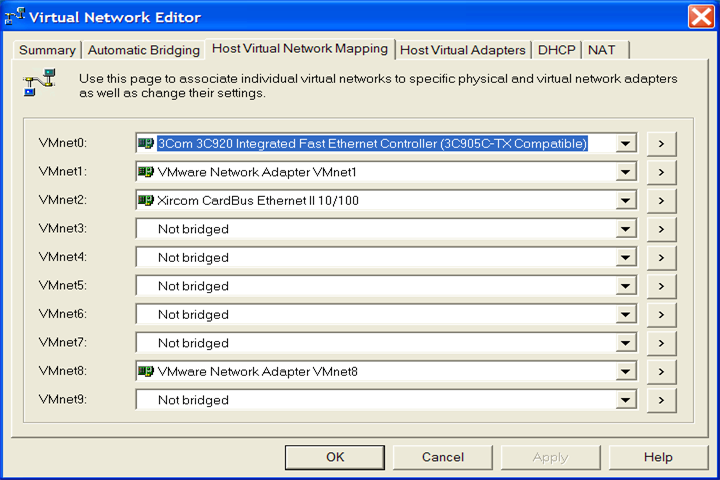
The logical to virtual to physical network adapter mappings shown above are:
- "eth0" <=> "vmnet0" <=> "3Com 3C920 Integrated Fast Ethernet Adapter"
- "eth1" <=> "vmnet2" <=> "Xircom CardBus Ethernet II 10/100 Adapter"
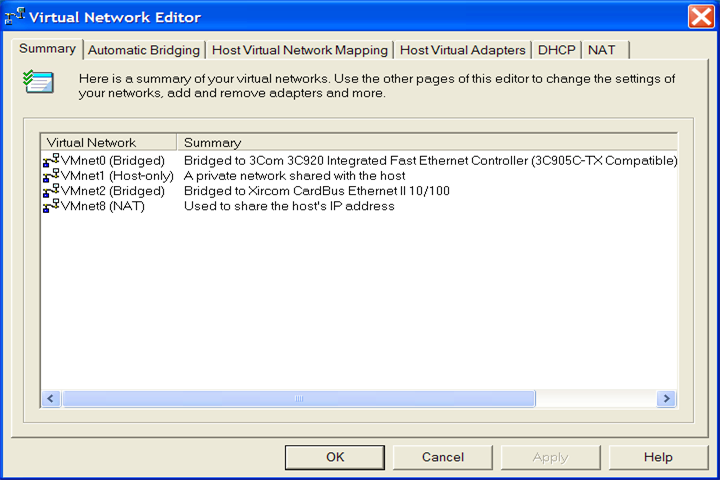
Once you have completed mapping each network adapter then use the "Virtual Network Editor" Summary tab to review your work:
Finally, after the NST Virtual Machine is started you will need to enable the additional network adapter you have just added for this guest virtual machine. It will most likely be in a disconnected state. Use the VMware Player menu bar to enable the virtual Ethernet device by changing its state to: connected.
How Do I Add More Than One Network Ethernet Adapter? (VMware Player: Linux)
![]() This information is outdated and does not pertain to the current NST release!
This information is outdated and does not pertain to the current NST release!
If your host Linux system is configured with more than one physical network adapter (Wired or Wireless) one can enable up to 4 network ethernet adapters with VMware Player. A NST Virtual Machine running under VMware Player host control can utilize each of the 4 network interfaces by running a different network/security application on each one of them.
The following sections cover the details on how to configure additional physical network adapters to be used with a NST Virtual Machine under a Linux-based VMware Player host.
The preconfigured Linux "vmx" VMware Player configuration file: "nst-vm-linux2.11.0.vmx" has 4 network ethernet interfaces already defined. Network interface: "eth0" will start in a "connected" state while network interfaces: "eth1", "eth2" and "eth3" will be started in the disconnected state. Network interface: "eth3" also has its "present" state set to "false". This allows for audio and sound usage with NST. If audio is not required, one can enable the "present" state to "true" for this interface. The connection type (connectionType) for each defined network ethernet interface is set to: "custom".
The following shows the predefined ethernet interface settings within the Linux "vmx" VMware Player configuration file:
ethernet0.present = "TRUE" ethernet0.virtualDev = "vmxnet" ethernet0.startConnected = "TRUE" ethernet0.connectionType = "custom" ethernet0.vnet = "/dev/vmnet0" ethernet1.present = "TRUE" ethernet1.virtualDev = "vmxnet" ethernet1.startConnected = "FALSE" ethernet1.connectionType = "custom" ethernet1.vnet = "/dev/vmnet2" ethernet2.present = "TRUE" ethernet2.virtualDev = "vmxnet" ethernet2.startConnected = "FALSE" ethernet2.connectionType = "custom" ethernet2.vnet = "/dev/vmnet3" ethernet3.present = "FALSE" ethernet3.virtualDev = "vmxnet" ethernet3.startConnected = "FALSE" ethernet3.connectionType = "custom" ethernet3.vnet = "/dev/vmnet4"
Each defined network adapter will assume a globally unique "MAC" address when the NST Virtual Machine is first booted up. This allows for multiple NST Virtual Machine instances to exist on the same physical network subnet without duplicate "ARP" entries being discovered.
The following shows an example of the globally unique "MAC" addresses and the "UUID" generated after the first time the NST Virtual Machine is started. This is typically generated at the end of the Linux "vmx" VMware Player configuration file.
ethernet0.addressType = "generated" ethernet1.addressType = "generated" ethernet2.addressType = "generated" uuid.location = "56 4d 21 a4 b2 4c cc ed-2d 17 2d 69 cf d4 fa 6d" uuid.bios = "56 4d 21 a4 b2 4c cc ed-2d 17 2d 69 cf d4 fa 6d" ethernet0.generatedAddress = "00:0c:29:d4:fa:6d" ethernet0.generatedAddressOffset = "0" ethernet1.generatedAddress = "00:0c:29:d4:fa:77" ethernet1.generatedAddressOffset = "10" ethernet2.generatedAddress = "00:0c:29:d4:fa:81" ethernet2.generatedAddressOffset = "20"
A mapping for each physical network adapter to a VMware Player virtual network adapter needs to occur. The preconfigured Linux "vmx" VMware Player configuration file: "nst-vm-linux2.11.0.vmx" has already defined the following logical ethernet to virtual network adapter mapping:
- "eth0" <=> "/dev/vmnet0"
- "eth1" <=> "/dev/vmnet2"
- "eth2" <=> "/dev/vmnet3"
- "eth3" <=> "/dev/vmnet4"
Use the "/usr/bin/vmware-config.pl" Linux VMware Player "VMware Configurator" script to perform the logical to virtual network adapter mapping. The results of running this script will be to start up a "bridge mapping" process for each network interface that needs to be mapped. Each mapping will be associated with a "Bridged" connection type. After all said and done the physical to logical (done by the Linux Kernel loadable network modules) to virtual network adapter (done by the "/usr/bin/vmware-config.pl" script) mapping will be completed.
Lets use a Linux VMware Player host system configured with 2 physical network ethernet adapters (in this case 2 gigabit ethernet adapters "eth0" and "eth1" adapter) to demostrate a physical to virtual network adapter mapping example:
First lets show what network interfaces are available using the "/sbin/ifconfig -a" command:
[root@striker ~]# /sbin/ifconfig -a
eth0 Link encap:Ethernet HWaddr 00:07:E9:0E:2B:7B
inet addr:10.222.222.14 Bcast:10.222.222.255 Mask:255.255.255.0
inet6 addr: fe80::207:e9ff:fe0e:2b7b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1075542 errors:0 dropped:0 overruns:0 frame:0
TX packets:910768 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:739987052 (705.7 MiB) TX bytes:413469820 (394.3 MiB)
Base address:0xdcc0 Memory:ff6e0000-ff700000
eth1 Link encap:Ethernet HWaddr 00:08:74:4F:EA:35
inet6 addr: fe80::208:74ff:fe4f:ea35/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1816456 errors:0 dropped:0 overruns:0 frame:0
TX packets:12 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:10
RX bytes:119424833 (113.8 MiB) TX bytes:984 (984.0 b)
Base address:0xdc80 Memory:ff6c0000-ff6e0000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:3956 errors:0 dropped:0 overruns:0 frame:0
TX packets:3956 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2504748 (2.3 MiB) TX bytes:2504748 (2.3 MiB)
sit0 Link encap:IPv6-in-IPv4
NOARP MTU:1480 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)
Next we will run the VMware Player "VMware Configurator" script: "/usr/bin/vmware-config.pl" to perform the mapping: (***Note: Only the network mapping output section is shown.)
[root@striker ~]# /usr/bin/vmware-config.pl
...
You have already setup networking.
Would you like to skip networking setup and keep your old settings as they are?
(yes/no) [no]
Do you want networking for your virtual machines? (yes/no/help) [yes]
Would you prefer to modify your existing networking configuration using the
wizard or the editor? (wizard/editor/help) [wizard]
The following bridged networks have been defined:
. vmnet0 is bridged to eth0
Do you wish to configure another bridged network? (yes/no) [no] yes
Configuring a bridged network for vmnet2.
The following bridged networks have been defined:
. vmnet0 is bridged to eth0
. vmnet2 is bridged to eth1
All your ethernet interfaces are already bridged.
Do you want to be able to use NAT networking in your virtual machines? (yes/no)
[yes] no
Do you want to be able to use host-only networking in your virtual machines?
[no]
Extracting the sources of the vmnet module.
Building the vmnet module.
Building for VMware Player 1.0.x or VMware Workstation 5.5.x.
Using 2.6.x kernel build system.
make: Entering directory `/tmp/vmware-config0/vmnet-only'
make -C /lib/modules/2.6.16-1.2108_FC4smp/build/include/.. SUBDIRS=$PWD SRCROOT=$PWD/. modules
make[1]: Entering directory `/usr/src/kernels/2.6.16-1.2108_FC4-smp-i686'
CC [M] /tmp/vmware-config0/vmnet-only/driver.o
CC [M] /tmp/vmware-config0/vmnet-only/hub.o
CC [M] /tmp/vmware-config0/vmnet-only/userif.o
CC [M] /tmp/vmware-config0/vmnet-only/netif.o
CC [M] /tmp/vmware-config0/vmnet-only/bridge.o
CC [M] /tmp/vmware-config0/vmnet-only/procfs.o
CC [M] /tmp/vmware-config0/vmnet-only/smac_compat.o
CC [M] /tmp/vmware-config0/vmnet-only/smac_linux.x386.o
LD [M] /tmp/vmware-config0/vmnet-only/vmnet.o
Building modules, stage 2.
MODPOST
CC /tmp/vmware-config0/vmnet-only/vmnet.mod.o
LD [M] /tmp/vmware-config0/vmnet-only/vmnet.ko
make[1]: Leaving directory `/usr/src/kernels/2.6.16-1.2108_FC4-smp-i686'
cp -f vmnet.ko ./../vmnet.o
make: Leaving directory `/tmp/vmware-config0/vmnet-only'
The module loads perfectly in the running kernel.
Starting VMware services:
Virtual machine monitor [ OK ]
Virtual ethernet [ OK ]
Bridged networking on /dev/vmnet0 [ OK ]
Bridged networking on /dev/vmnet2 [ OK ]
The configuration of VMware Player 1.0.1 build-19317 for Linux for this running
kernel completed successfully.
You can now run VMware Player by invoking the following command:
"/usr/bin/vmplayer".
...
At this point the mapping should be completed using the "Bridged" connection type. One can perform a check by searching for running VMware Player "vmnet-bridge" processes:
[root@striker ~]# /bin/ps -ef|grep "vmnet-bridge"
root 25526 1 0 07:33 pts/3 00:00:00 /usr/bin/vmnet-bridge -d /var/run/vmnet-bridge-0.pid /dev/vmnet0 eth0
root 25530 1 0 07:33 pts/3 00:00:00 /usr/bin/vmnet-bridge -d /var/run/vmnet-bridge-2.pid /dev/vmnet2 eth1
Finally, after the NST Virtual Machine is started you will need to enable the additional network adapter you have just added for this guest virtual machine. It will most likely be in a disconnected state. Use the VMware Player menu bar to enable the virtual ethernet device by changing its state to: connected.
What Are The Advantages Of Using VMware Server Instead of VMware Player?
The following details the advantages of using VMware Server™ over VMware Player™:
- It allows you to power on virtual machines at system boot. For example, it is possible to turn on a Windows machine with VMware Server™ installed and have the NST Virtual Machine automatically started (you don't need to touch anything but the power button - logging into Windows is not required).
- It allows you to start/stop/use virtual machines from remote computers.
- It allows you to allocate more than one CPU to a virtual machine.
- It provides a full GUI virtual machine editor whereas you need to edit your VMX files in a text editor when using VMware Player™.